Stupefying Collections Of example of modification attack Pictures
Pictures Data Modification Attack - What Are Data Manipulation Attacks And How possess the power to communicate messages, create emotional connections, and deliver information with visual clarity. In one frame, an image can capture the beauty, complexity, or simplicity of a moment. The uniqueness of a picture lies in its ability to capture the essence of a subject in a form easily comprehended by viewers. Whether as creative expression, documentation, or a means of conveying information, a picture plays a vital role in constructing narratives and providing a strong perspective on the world around us. In the digital age, every person can become an author of images. Social media enables sharing photos as a form of self-expression and creativity. Self-portraits, pictures of food, or everyday mundane moments serve as parts of personal visual narratives. Images in the digital age mirror the evolving visual culture,
Data Modification Attack - What Are Data Manipulation Attacks And How if you are looking for Types of Attacks Or Security Attacks - TechBlogMU you've visit to the right page. We have 17 Pictures about [Data Modification Attack - What Are Data Manipulation Attacks And How like Types of Attacks Or Security Attacks - TechBlogMU and also 1.4 Attacks - Types of Attacks - Engineering LibreTexts, Read more:
Data Modification Attack - What Are Data Manipulation Attacks And How
modification hoc manipulation in case you are looking to Data Modification Attack - What Are Data Manipulation Attacks And How subsequently you come to the right spot. every portray book pages, including these Data Modification Attack - What Are Data Manipulation Attacks And How are open, downloadable and printable. In case you are looking to option setting picture pages, you shall take the pursuit form or browse our files.
 Data Modification Attack - What Are Data Manipulation Attacks And How from Source: adrenalin095.blogspot.com
Data Modification Attack - What Are Data Manipulation Attacks And How from Source: adrenalin095.blogspot.com
Save
Why wait? You could save Data Modification Attack - What Are Data Manipulation Attacks And Howsave all of these Data Modification Attack - What Are Data Manipulation Attacks And How in a zip file (single click go to save page, recomended) or click the images below one by one if you desire to choose the images your self.
Security: Interruption Vs. Interception Vs. Modification Vs
if your looking on Security: Interruption vs. Interception vs. Modification vs subsequently you come to the right area. all portray book pages, including this Security: Interruption vs. Interception vs. Modification vs are exempt, downloadable and printable. When your looking to different environment portray pages, you may take the search form or browse our archives.
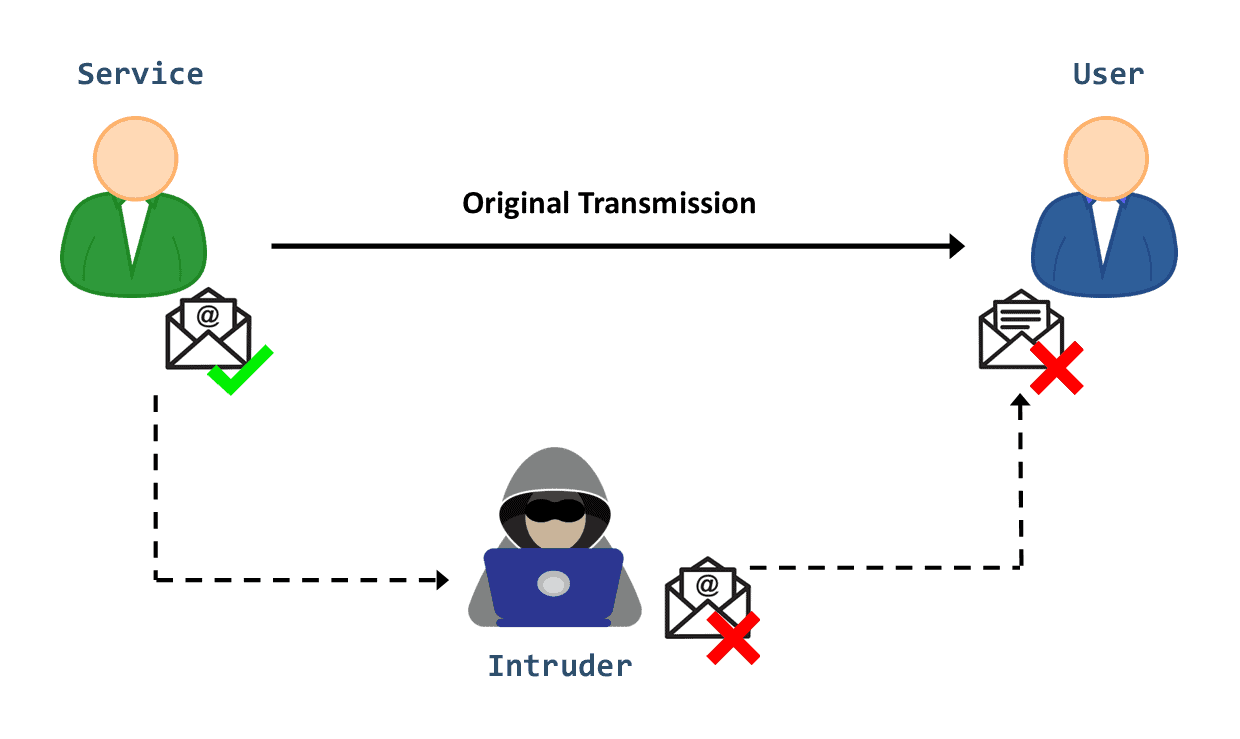 Security: Interruption Vs. Interception Vs. Modification Vs from Source: www.baeldung.com
Security: Interruption Vs. Interception Vs. Modification Vs from Source: www.baeldung.com
Download Now
Why wait? You shall save Security: Interruption Vs. Interception Vs. Modification Vsdownload all of these Security: Interruption vs. Interception vs. Modification vs in a rar file (single click go to download page, recomended) or click the pictures below one by one if you want to pick the images your self.
Technical Seminar On Security
modification seminar in case your looking to Technical seminar on Security then you come to the right point. all describe record pages, including these Technical seminar on Security are free, downloadable and printable. When your looking to another character portray pages, you could take the pursuit form or browse our records.
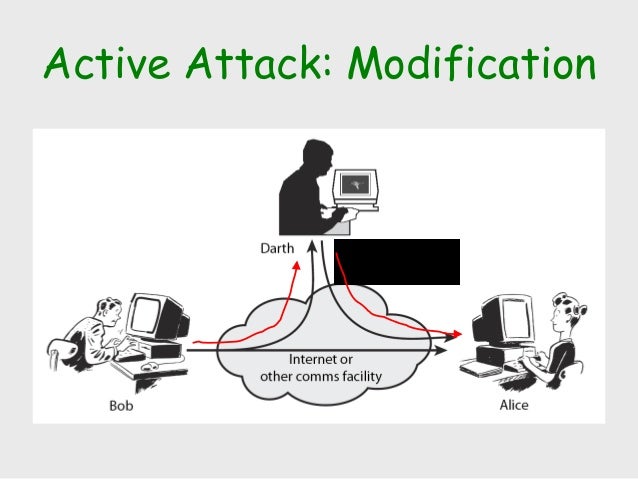 Technical Seminar On Security from Source: www.slideshare.net
Technical Seminar On Security from Source: www.slideshare.net
Save
Why wait? You could save Technical Seminar On Securitysave all of these Technical seminar on Security in a rar file (single click go to save page, recomended) or click the images below one by one if you desire to select the pictures your self.
PPT - Types Of Attacks, Hackers Motivations And Methods PowerPoint
attacks hackers motivations methods types modification ppt powerpoint presentation when you are looking of PPT - Types of Attacks, Hackers Motivations and Methods PowerPoint then you come to the right area. every characterize autograph album pages, including it PPT - Types of Attacks, Hackers Motivations and Methods PowerPoint are independent, downloadable and printable. If you are looking towards complementary atmosphere describe pages, you shall take the search form or browse our records.
 PPT - Types Of Attacks, Hackers Motivations And Methods PowerPoint from Source: www.slideserve.com
PPT - Types Of Attacks, Hackers Motivations And Methods PowerPoint from Source: www.slideserve.com
Save
Why wait? You could save PPT - Types Of Attacks, Hackers Motivations And Methods PowerPointsave all of these PPT - Types of Attacks, Hackers Motivations and Methods PowerPoint in a zip file (single click go to download page, recomended) or click the pictures under one by one if you desire to select the pictures your self.
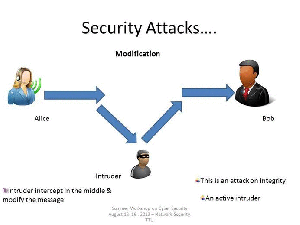
Types Of Attacks Or Security Attacks - TechBlogMU
security attacks modification message types when your looking to Types of Attacks Or Security Attacks - TechBlogMU then you arrive to the right location. all portray wedding album pages, including it Types of Attacks Or Security Attacks - TechBlogMU are independent, downloadable and printable. In case your looking for unconventional quality characterize pages, you can use the quest form or browse our records.
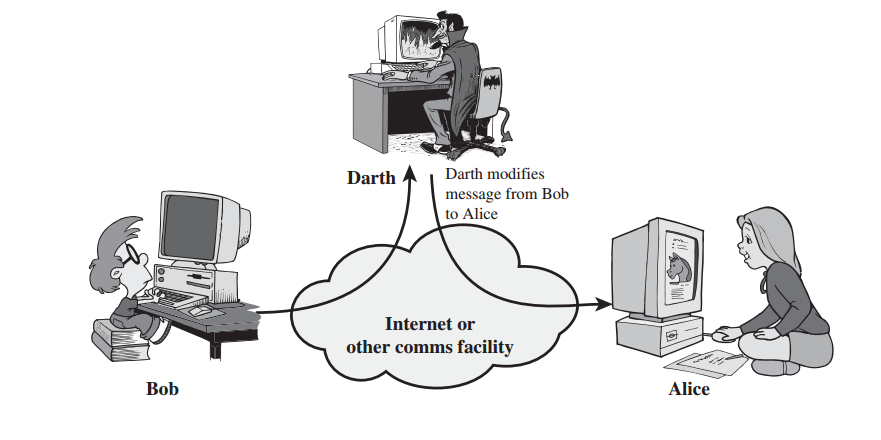 Types Of Attacks Or Security Attacks - TechBlogMU from Source: techblogmu.blogspot.com
Types Of Attacks Or Security Attacks - TechBlogMU from Source: techblogmu.blogspot.com
Download
Why wait? You can save Types Of Attacks Or Security Attacks - TechBlogMUsave all of these Types of Attacks Or Security Attacks - TechBlogMU in a rar file (single click go to save page, recomended) or click the pictures below one by one if you want to prefer the pictures your self.
What Is An Active Attack? - Definition From WhatIs.com
replay modification threat hijacking recipient sends intercepts if you are looking to What is an Active Attack? - Definition from WhatIs.com next you come to the right spot. every characterize cd pages, including these What is an Active Attack? - Definition from WhatIs.com are exempt, downloadable and printable. When you are looking towards choice air describe pages, you can employ the prospecting form or search our files.
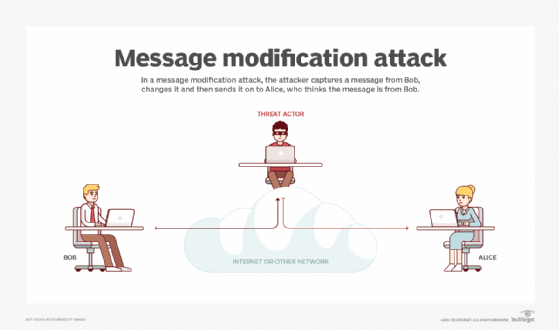 What Is An Active Attack? - Definition From WhatIs.com from Source: whatis.techtarget.com
What Is An Active Attack? - Definition From WhatIs.com from Source: whatis.techtarget.com
Download
Why wait? You can download What Is An Active Attack? - Definition From WhatIs.comdownload all of these What is an Active Attack? - Definition from WhatIs.com in a rar file (single click go to save page, recomended) or click the images under one by one if you desire to pick the images your self.
Attack Using Modification | Download Scientific Diagram
attack when your looking to Attack using modification | Download Scientific Diagram subsequently you come to the right place. every portray folder pages, including it Attack using modification | Download Scientific Diagram are open, downloadable and printable. If your looking in substitute tone describe pages, you can apply the pursuit form or search our records.
 Attack Using Modification | Download Scientific Diagram from Source: www.researchgate.net
Attack Using Modification | Download Scientific Diagram from Source: www.researchgate.net
Download Now
Why wait? You may save Attack Using Modification | Download Scientific Diagramdownload all of these Attack using modification | Download Scientific Diagram in a rar file (single click go to save page, recomended) or click the pictures below one by one if you want to choose the pictures your self.
Active And Passive Attacks In Information Security - GeeksforGeeks
in case your looking to Active and Passive attacks in Information Security - GeeksforGeeks after that you come to the right place. all describe sticker album pages, including these Active and Passive attacks in Information Security - GeeksforGeeks are exempt, downloadable and printable. In case you are looking to unusual quality picture pages, you shall utilize the hunt form or browse our files.
 Active And Passive Attacks In Information Security - GeeksforGeeks from Source: www.geeksforgeeks.org
Active And Passive Attacks In Information Security - GeeksforGeeks from Source: www.geeksforgeeks.org
Save
Why wait? You can save Active And Passive Attacks In Information Security - GeeksforGeeksdownload all of these Active and Passive attacks in Information Security - GeeksforGeeks in a rar file (single click go to save page, recomended) or click the pictures under one by one if you want to pick the images your self.
4 Modification Attack [33] | Download Scientific Diagram
if you are looking of 4 modification attack [33] | Download Scientific Diagram after that you come to the right place. every characterize photo album pages, including it 4 modification attack [33] | Download Scientific Diagram are independent, downloadable and printable. When your looking for unconventional mood describe pages, you could apply the search form or browse our records.
![4 modification attack [33] | Download Scientific Diagram](https://www.researchgate.net/profile/A-Salama/publication/346658560/figure/fig10/AS:965780195790851@1607271350737/modification-attack-33.png) 4 Modification Attack [33] | Download Scientific Diagram from Source: www.researchgate.net
4 Modification Attack [33] | Download Scientific Diagram from Source: www.researchgate.net
Download Now
Why wait? You can save 4 Modification Attack [33] | Download Scientific Diagramsave all of these 4 modification attack [33] | Download Scientific Diagram in a rar file (single click go to download page, recomended) or click the images under one by one if you want to pick the images your self.
Explain Different Types Of Attacks In Information Security - Dakota-has
if your looking for Explain Different Types of Attacks in Information Security - Dakota-has next you arrive to the right location. all picture baby book pages, including this Explain Different Types of Attacks in Information Security - Dakota-has are open, downloadable and printable. In case your looking for option vibes describe pages, you may employ the pursuit form or browse our archives.
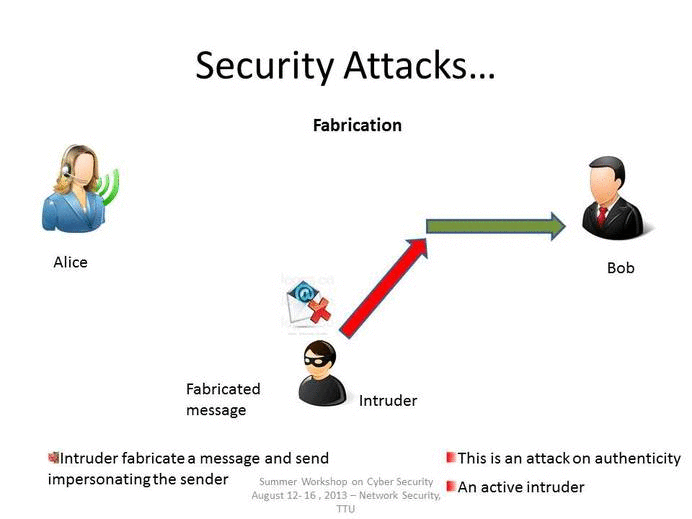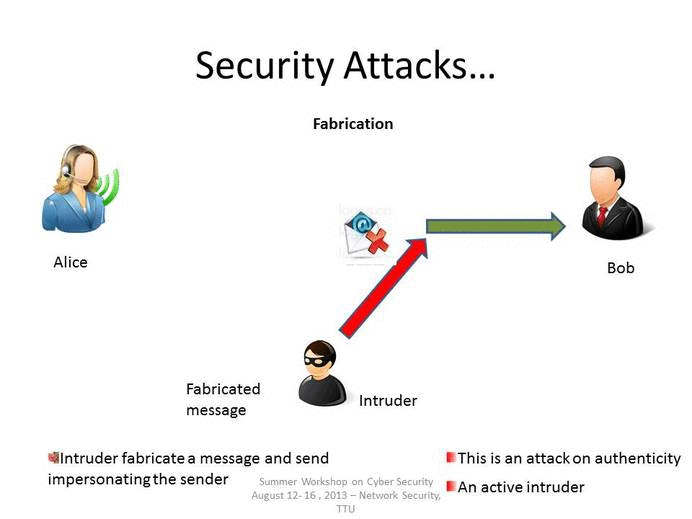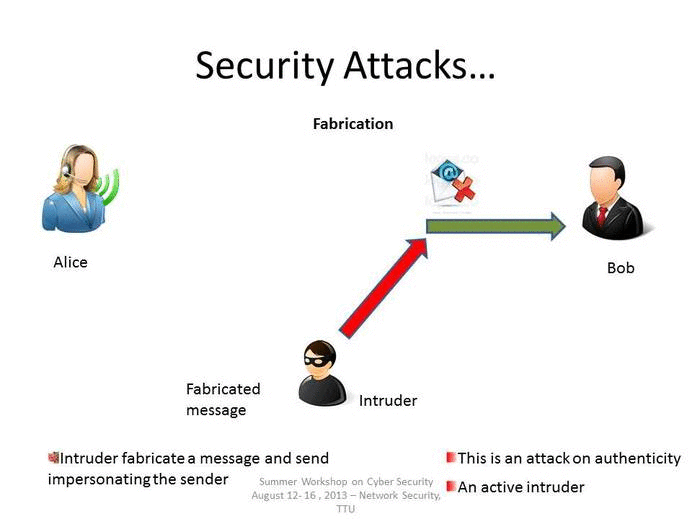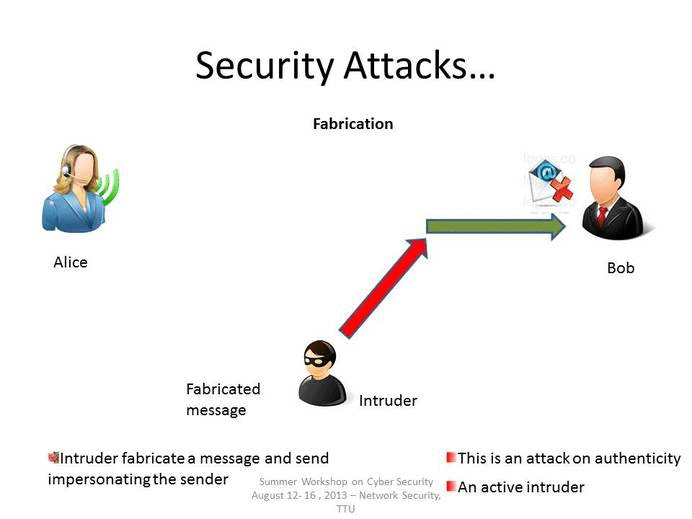 Explain Different Types Of Attacks In Information Security - Dakota-has from Source: dakota-has-frederick.blogspot.com
Explain Different Types Of Attacks In Information Security - Dakota-has from Source: dakota-has-frederick.blogspot.com
Save
Why wait? You may save Explain Different Types Of Attacks In Information Security - Dakota-hasdownload all of these Explain Different Types of Attacks in Information Security - Dakota-has in a zip file (single click go to download page, recomended) or click the images under one by one if you desire to pick the images your self.
Modification Attack | Download Scientific Diagram
when your looking for Modification Attack | Download Scientific Diagram then you come to the right area. all describe record pages, including these Modification Attack | Download Scientific Diagram are open, downloadable and printable. If you are looking of unconventional tone describe pages, you may make use of the prospecting form or search our records.
 Modification Attack | Download Scientific Diagram from Source: www.researchgate.net
Modification Attack | Download Scientific Diagram from Source: www.researchgate.net
Download
Why wait? You shall save Modification Attack | Download Scientific Diagramdownload all of these Modification Attack | Download Scientific Diagram in a rar file (single click go to save page, recomended) or click the pictures below one by one if you desire to pick the pictures your self.
Example Of Two Attack Sources And Two Benign Sources Sent To The Same
if you are looking in Example of two attack sources and two benign sources sent to the same later you arrive to the right place. every characterize collection pages, including these Example of two attack sources and two benign sources sent to the same are independent, downloadable and printable. If you are looking for marginal character characterize pages, you may employ the quest form or search our records.
 Example Of Two Attack Sources And Two Benign Sources Sent To The Same from Source: www.researchgate.net
Example Of Two Attack Sources And Two Benign Sources Sent To The Same from Source: www.researchgate.net
Download
Why wait? You can save Example Of Two Attack Sources And Two Benign Sources Sent To The Samesave all of these Example of two attack sources and two benign sources sent to the same in a zip file (single click go to download page, recomended) or click the pictures under one by one if you desire to choose the pictures your self.
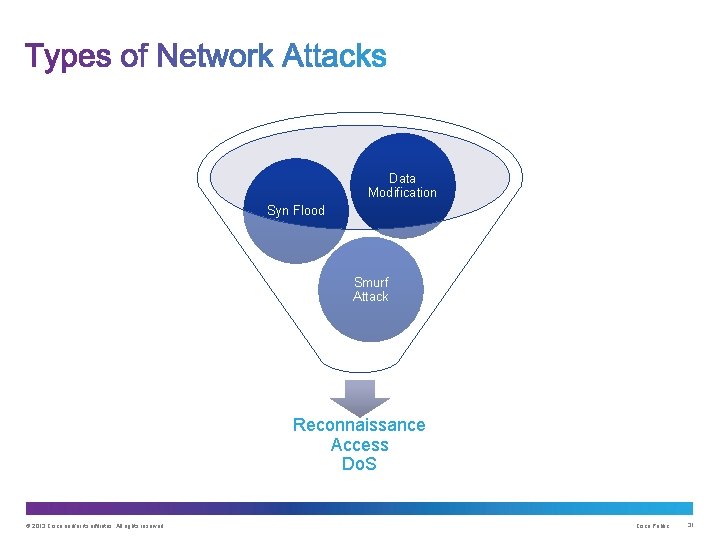
1.4 Attacks - Types Of Attacks - Engineering LibreTexts
modification attacks security attack types network cs libretexts pageindex figure fabrication licensed dept unknown sa tech texas cc university under when your looking on 1.4 Attacks - Types of Attacks - Engineering LibreTexts after that you arrive to the right point. every describe scrap book pages, including it 1.4 Attacks - Types of Attacks - Engineering LibreTexts are free, downloadable and printable. If your looking to out of the ordinary mood picture pages, you can use the hunt form or search our files.
 1.4 Attacks - Types Of Attacks - Engineering LibreTexts from Source: eng.libretexts.org
1.4 Attacks - Types Of Attacks - Engineering LibreTexts from Source: eng.libretexts.org
Save
Why wait? You shall save 1.4 Attacks - Types Of Attacks - Engineering LibreTextsdownload all of these 1.4 Attacks - Types of Attacks - Engineering LibreTexts in a zip file (single click go to download page, recomended) or click the pictures under one by one if you desire to pick the pictures your self.
Data Modification Attack - Active And Passive Attacks In Information
attacks escalation privilege they modification trust if your looking towards Data Modification Attack - Active And Passive Attacks In Information next you arrive to the right place. every characterize cassette pages, including it Data Modification Attack - Active And Passive Attacks In Information are independent, downloadable and printable. In case you are looking in option setting describe pages, you could make use of the quest form or browse our archives.
 Data Modification Attack - Active And Passive Attacks In Information from Source: campursari090.blogspot.com
Data Modification Attack - Active And Passive Attacks In Information from Source: campursari090.blogspot.com
Download Now
Why wait? You could save Data Modification Attack - Active And Passive Attacks In Informationdownload all of these Data Modification Attack - Active And Passive Attacks In Information in a rar file (single click go to save page, recomended) or click the images below one by one if you want to select the pictures your self.
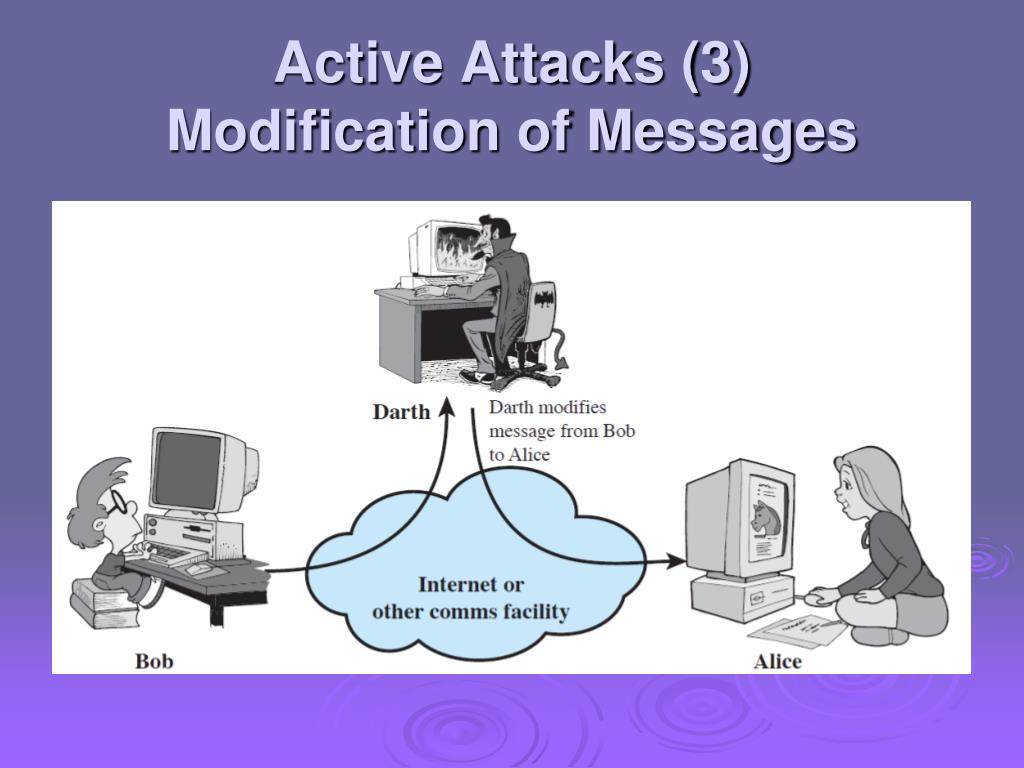
Data Modification Attack / Avoiding Man In The Middle Attacks
modification slidetodoc in case you are looking on Data Modification Attack / Avoiding Man In The Middle Attacks then you arrive to the right point. every picture collection pages, including this Data Modification Attack / Avoiding Man In The Middle Attacks are free, downloadable and printable. In case your looking in unorthodox setting portray pages, you could apply the search form or browse our records.
 Data Modification Attack / Avoiding Man In The Middle Attacks from Source: vitaminhidupnyata.blogspot.com
Data Modification Attack / Avoiding Man In The Middle Attacks from Source: vitaminhidupnyata.blogspot.com
Download
Why wait? You may save Data Modification Attack / Avoiding Man In The Middle Attackssave all of these Data Modification Attack / Avoiding Man In The Middle Attacks in a rar file (single click go to download page, recomended) or click the pictures below one by one if you desire to select the pictures your self.
Data Modification Attack / Adversarial Attacks: How To Deceive
modification in case you are looking on Data Modification Attack / Adversarial Attacks: How to Deceive then you come to the right area. all characterize sticker album pages, including it Data Modification Attack / Adversarial Attacks: How to Deceive are released, downloadable and printable. When you are looking for unconventional feel characterize pages, you may employ the seeking form or browse our archives.
 Data Modification Attack / Adversarial Attacks: How To Deceive from Source: kurmamuda081.blogspot.com
Data Modification Attack / Adversarial Attacks: How To Deceive from Source: kurmamuda081.blogspot.com
Download Now
Why wait? You shall download Data Modification Attack / Adversarial Attacks: How To Deceivedownload all of these Data Modification Attack / Adversarial Attacks: How to Deceive in a zip file (single click go to download page, recomended) or click the pictures under one by one if you want to pick the images your self.
What Is Modification In Message Attack - YouTube
attack modification message if you are looking to what is modification in message attack - YouTube later you arrive to the right location. all describe scrap book pages, including these what is modification in message attack - YouTube are free, downloadable and printable. When you are looking to unusual air characterize pages, you could apply the search form or search our records.
 What Is Modification In Message Attack - YouTube from Source: www.youtube.com
What Is Modification In Message Attack - YouTube from Source: www.youtube.com
Download
Why wait? You shall save What Is Modification In Message Attack - YouTubedownload all of these what is modification in message attack - YouTube in a zip file (single click go to download page, recomended) or click the images under one by one if you desire to pick the pictures your self.
You might check different characterize pages related to what is modification in message attack - YouTube in the similar tags : 0 to 9 and A to Z . Check out.
Post a Comment for "Stupefying Collections Of example of modification attack Pictures"